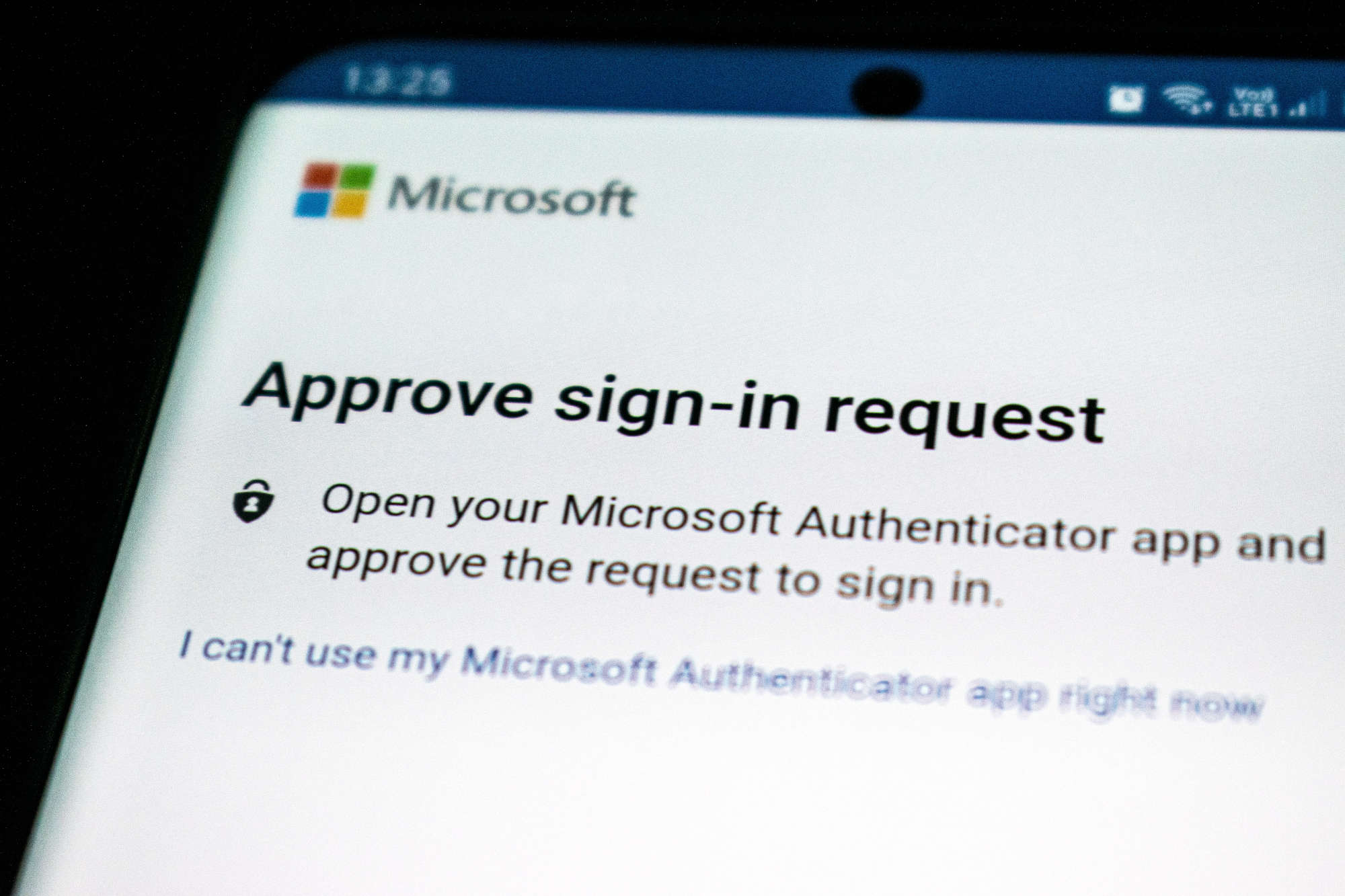
Passkey is hot right now, so we thought we’d write a quick overview.
So what is Passkey?
Passkey-based authentication is a security mechanism where a user or a system is granted access to a resource or service using a unique and temporary passkey. The passkey is a secret value, typically a string of characters or a cryptographic token, that is used to verify the identity of the user or system. The main idea behind passkey-based authentication is to provide a secure and convenient alternative to traditional username and password-based authentication schemes.
How it works
Here’s an overview of how passkey-based authentication works:
- A user or system requests access to a protected resource or service.
- The authentication system generates a unique and temporary passkey for the user or system.
- The passkey is sent to the user or system via a secure communication channel, such as email, SMS, or a secure messaging app.
- The user or system provides the received passkey to the authentication system.
- The authentication system verifies the correctness and validity of the passkey.
- If the passkey is correct and valid, the user or system is granted access to the requested resource or service.
Why use it
Passkey-based authentication has several benefits:
- Enhanced Security: Passkeys are typically generated using cryptographically secure random number generators, making them difficult to guess or crack.
- Temporary Access: Passkeys are usually time-limited, which means they expire after a certain period or after being used, reducing the risk of unauthorized access.
- Convenience: Users don’t have to remember complex passwords; they only need to provide the passkey they receive via the communication channel.
What are the issues
Passkey-based authentication has some drawbacks:
- Reliance on External Channels: The authentication process depends on the security and reliability of the communication channel used to deliver the passkey.
- Potential for Phishing: Attackers may attempt to trick users into revealing their passkeys by impersonating the authentication system.
- Inconvenience: Users may find it bothersome to repeatedly request and enter passkeys for authentication.
Despite these drawbacks, passkey-based authentication can be an effective security measure when implemented correctly and combined with other authentication methods, such as multi-factor authentication (MFA) or risk-based authentication.
Learn More
Contact us to learn more.